
Summary:
- Ransomware is a family of malware that blocks access to a PC, server or mobile device, or encrypts all the data stored on that machine.
- Get and manage a backup system BEFORE you get hit with Ransomware!
- Ransomware is a growing threat to businesses of all sizes.
- A 2016 IBM survey of 600 businesses shows that nearly half of the executives surveyed said their company had experienced a ransomware attack and 70 percent of the businesses infected with ransomware had paid a ransom.
- The Locky ransomware program now has Facebook and LinkedIn vulnerabilities, and is can place files, typically in the form of images, from social media sites onto on your computer, according to Ars Technica.
- Most Ransomware is spread through spoof emails opened by employees.
- If you are affected by ransomware, file a report via the FBI’s Internet Crime Complaint Center.
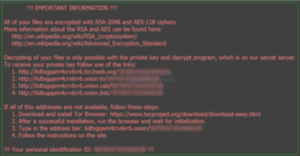
Photo from Ars Technica report on Locky ransomware, 2/18/16.
Ransomware payments for 2016 are expected to hit a billion dollars, per the FBI. That compares to just $24 million paid in 2015. And it’s expected to get even worse this year. Big and medium-sized companies are more attractive extortion victims, since they can pay a bigger ransom, however, an IBM report says small businesses are also at risk because their employees often lack training in workplace IT security. The study found that only 30 percent of the 200 small businesses surveyed offer security training to their employees, compared to 58 percent of larger companies.
Ransomware is a family of malware that blocks access to a PC, server or mobile device, or encrypts all the data stored on that machine. It’s typically delivered via malicious email or infected third-party websites. To regain access or control of the data, the user must pay a ransom — typically via bitcoin. The encryption is unbreakable and simply removing the malware will not solve the problem. The victim is forced to pay for the unique software key that will unlock everything. Malwarebytes reports that 60 percent of all malware observed last year was ransomware.
One high-profile ransomware attack happened on January 22 to a luxury hotel in Austria. According to Digital Trends, the hotel paid about $1,600 in bitcoin to retrieve its electronic key card systems. The hotel has been targeted numerous times by ransomware attacks, but decided to go public with this information as a warning to other small businesses.
Experts warn businesses not to pay ransomware because it encourages this activity and there is no guarantee that the systems and data will be restored. Digital Trends reports that, “The hotel almost learned this the hard way, as the cybercriminals attempted yet another attack after the ransom was paid. That attempt was only thwarted by the installation of new hardware.”
The St. Louis public library system was also attacked recently by ransomware that took down circulation and public access computers at all of their 16 library branches, according to the St. Louis Post Dispatch. The hackers demanded a $35,000 ransom to free up the 700+ computers. The library was able to refuse paying because it had a robust back-up and recovery system which allowed library IT staff to restore the affected servers after fully wiping them.
Ransomware is a growing threat to businesses of all sizes. A 2016 IBM survey of 600 businesses shows that nearly half of the executives surveyed said their company had experienced a ransomware attack and 70 percent of the businesses infected with ransomware had paid a ransom. Ransom was more than $10,000 for half of those businesses that paid.
How do you protect yourself from ransomware?
- Don’t open attachments from an unknown sender. IBM found that nearly 40 percent of all spam emails sent in 2016 contained ransomware. Be particularly careful with zip files and images that you did not download. If you see a new image or graphic file on your computer that you don’t recall downloading, do not open it. The Locky ransomware program now has Facebook and LinkedIn vulnerabilities, and is can place files, typically in the form of images, from social media sites onto on your computer, according to Ars Technica.
- Make sure your saved data is being backed up daily. Ask your IT team to confirm if the location where your data is being saved is backed up to avoid any uncertainty about nwhether your data is safe.
- Don’t assume your desktop or laptop is being backed up. If you have not been told by your IT team that your desktop or laptop, specifically, is backed up, assume it is not and do not save irreplaceable data there.
- Reassess your data backup and restoration process. Ask your IT team how far back backups go and test it out. Create a test file, allow for it to be backed up and then delete it. Wait a week or two and ask for it to be restored. This should clarify the scope and history of the backup in place and allow you to review the process for requesting a file to be restored.
- Update, patch and purge. You should be set to receive automatic security updates and patches for all software, including operating systems, apps and security software — on all devices. Delete any applications that you rarely or never use.
- Disable those macros. IBM reports that document macros are now a common way to deliver ransomware, so macros for email and documents should be disabled by default.
- Don’t pick up or use USBs from an unknown source. Hackers are now using USBs to spread ransomware so don’t use USBs you find or borrow or from free giveaways at conferences as you don’t know whether they are infected. If an infected USB is plugged into the computer port, it will install malicious code onto the computer, infecting it and any device on an unprotected network.
- Contact the FBI if you are affected. If you are affected by ransomware, file a report via the FBI’s Internet Crime Complaint Center. The FBI also has tips for protecting yourself and your organization.
- Provide security training to your employees. The greatest threats to our data security can come through email, but spoof emails and phishing scams are getting harder to detect, especially when they come with a logo from your local bank or another trusted company. According to the 2014 McAfee Labs Threats Report, 80% of business users failed to spot a malicious email. Understanding how to recognize and handle these types of threats, as well as sharing this information within your organization, could help mitigate the risk of a data breach.
Contact THB for more information on how to create a culture of data security in your organization.

Comments are closed.